Why LOG SLEUTH?
IT system logs are necessary for many businesses to maintain and review in order to identify errors, anomalous activity, or unauthorized access. The entire organization benefits from this. By using, LOG SLEUTH, you can save time and money by identifying issues early on.
Our tool helps IT and security teams fix issues in systems and apps by analyzing logs. It also enables them to assess performance and identify areas for improvement.
Our tool also helps security teams to find suspicious activities, strange behaviour, or unauthorized access attempts, so they can respond quickly and reduce risks.
The Challenge
- Gathering all kinds of logs from various sources into one place.
- Converting different logs into a standard normalize format, eventually making it easy to understand.
- Finding patterns or unusual things, like a cyber-attack, by looking at all the logs together.
LOG SLEUTH Solution
- Gathering all kinds of logs from various sources into one place.
- Converting different logs into a standard normalize format, eventually making it easy to understand.
- Finding patterns or unusual things, like a cyber-attack, by looking at all the logs together.
Results & Benefits
- Keep an eye on all logs from various sources from centralized location.
- Get automatic alerts when something suspicious activity is found, so you can generate notification.
- Use LOG SLEUTH to detect illegal access attempts and verify that security operations and firewalls are configured properly.
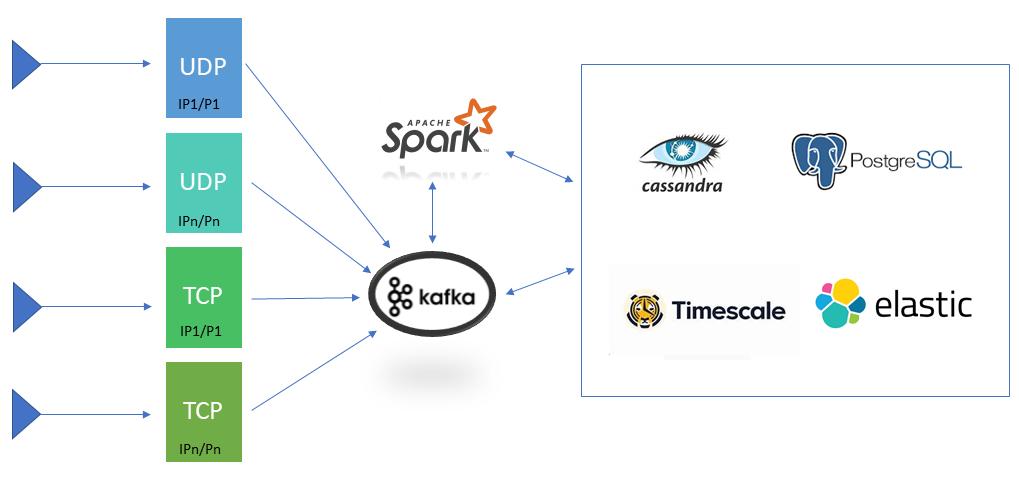
LOG SLEUTH in Action
LOG SLEUTH is a versatile and robust system that can scale with your evolving requirements. Additionally, it offers significant cost savings and can be seamlessly integrated across various environments. Furthermore, it can store and access data in a way that best suits your needs. LOG SLEUTH can collect data from many different sources, like system logs, network logs, application logs, SNMP, MS Event Logs and etc.
These collectors aggregate logs from different sources, such as network devices, servers and firewalls to help identify connections between them. This helps reveal hidden patterns and clues that might show a potential cyberattack. LOG SLEUTH uses advanced AI and machine learning algorithm to find unusual patterns in the data, so you can catch problems before they become big issues.
LOG SLEUTH can work with many different types of messaging protocols and can be set up in an easiest way that makes it very reliable and scalable. It can also be configured in a cluster to ensure it is always available and can handle large amounts of data.
LOG SLEUTH deliver messages at network limited throughput using a cluster of machines with latencies. LOG SLEUTH is capable of scaling production clusters up to a thousand brokers, processing trillions of messages per day, storing huge amount of data, and managing hundreds of thousands of partitions. It securely stores data streams in a reliable, fault-tolerant system that can withstand failures.
LOG SLEUTH spreads out its resources across different locations to ensure high availability and can also connect multiple locations together.
LOG SLEUTH Benefits
- Enhanced Security Posture: LOG SLEUTH plays an important role in securing your defenses by proactively identifying and addressing weaknesses before malicious actors can make use of them.
- Compliance Assurance: Generate detailed reports that align with regulatory requirements, ensuring Compliance with standards like GDPR, HIPAA, etc.
- Operational Efficiency: LOG SLEUTH helps organizations identify and fix problems quickly by analyzing logs to find errors and trends across different teams and departments.
- Risk Mitigation: LOG SLEUTH helps prevent costly security breaches by catching and fixing problems early.
Global Professionals
LOG SLEUTH is recommended because it helps companies catch problems early, saving time and money. It also helps take quick action to prevent small issues from becoming big problems that cause downtime.
