Why CVA?
In today’s digital world, any organization must regularly perform vulnerability assessments to identify the weaknesses and fix them before they are exploited and thus ensure protection over sensitive data. By considering threats, assessments reduce the risk of breaches, financial loss and thus helping to strengthen overall cyber security resilience.
Theory of Operation
Vulnerability Assessment takes a structured, AI-powered approach to scan your whole IT environment, identifying hidden weakness in networks, systems, and applications. The AI engine eliminates false positives and uses advanced methods to detect vulnerabilities often missed by traditional tools. It then prioritizes these risks based on severity and system importance, ensuring efficient remediation. This ongoing, iterative process helps you stay ahead of evolving threats, improving your security posture and minimizing risk.
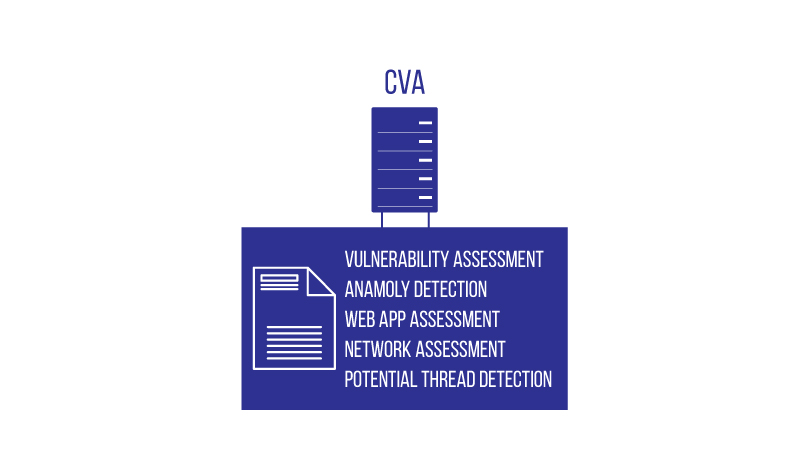
Type of Vulnerability Assessment Modules
- Comprehensive Vulnerability Assessment
- Advanced Threat Detection and Analysis
- Endpoint Security and Network Scanning
- Web Application Security
- Comprehensive Security Reporting and Analysis
Comprehensive Vulnerability Assessment
This module uses proprietary databases and industry standards to quickly and accurately identify security risks, automating threat detection to help organizations to address vulnerabilities and enhance their security.
- Identify risks via database
- Integrates CVE and OWASP
- Covers all vulnerabilities
- Automates faster assessments
- Ensures complete coverage
Advanced Threat Detection and Analysis
This module identifies vulnerabilities using advanced techniques, prioritizing threats by severity to help organizations respond quickly and mitigate risks before they are exploited.
- Uncovers hidden vulnerabilities
- Prioritizes threats for remediation
- Provides attack vector insights
- Identifies critical threats early
- Enables proactive risk mitigation
Endpoint Security and Network Scanning
This module protects against unauthorized access and malware, identifies vulnerabilities through network scans, and enables proactive threat detection with real-time monitoring to strengthen security.
- Protects endpoints from threats
- Scans networks for vulnerabilities
- Detects breaches early
- Provides real-time monitoring
- Safeguard all endpoints
Web Application Security
This module identifies and addresses web-specific vulnerabilities, aligns with OWASP top 10 standards, and provides actionable insights to developers to fix code level vulnerability and strengthen application security.
- Addresses web application vulnerabilities
- Identifies XSS and common flaws
- Aligns with OWASP top 10 standards
- Provides insights for remediation
- Strengthens security by identifying weaknesses
Comprehensive Security Reporting and Analysis
This module provides detailed vulnerability reports with severity levels, actionable remediation steps and streamlines compliance and audits to improve security and maintain regulatory standards.
- Generates detailed vulnerability reports
- Prioritizes critical risks
- Provides actionable remediation steps
- Simplifies compliance with documentation
- Supports efficient audit readiness
