

Our mission is to simplify and streamline cyber security for IT and administrative team across various industries and organizations, reducing their workload while ensuring efficiency and effectiveness in safeguarding systems.
At TectonaS we also understand that the needs of IT networks differ between small and large organizations. Therefore, we ensure that our cybersecurity platforms and software are adaptable and customizable to align with the unique and evolving requirements of each organizations.
Based in India, TectonaS specializes in Cyber Security Audit Automation, developing make in India product that offer flexible and customizable solutions tailored to varying organizational needs. Our approach focuses on problem-solving, with a team experienced in securing over 200 clients across 8 countries. Our products are user-friendly, compatible with Windows, Linux and Mac and accessible to both business owners and IT managers.
All OwnYit products by TectonaS are designed in a way that it can be adapted to the varying needs of an organization.
At TectonaS, we recognize that each situation is unique, which is why we thoroughly analyze the problem areas and provide customized solutions to address them effectively.
We design our products to be user friendly, requiring no technical expertise to operate. They are suitable for both business owners and IT managers, with the option for role-based access control.
All our products are compatible with operating systems like Windows, Linux as well as Mac.
Our products are distributed through a network of exclusive dealers, distributors and delivery partners strategically located across India.
Our ENDEC team, comprising highly trained and skilled professionals, has successfully secured over 200 clients across 8 countries. The team has enhanced IT visibility, reduced operational costs, mitigated cyber security threats, ensured compliance with cybersecurity standards and delivered a range of other impactful solutions.
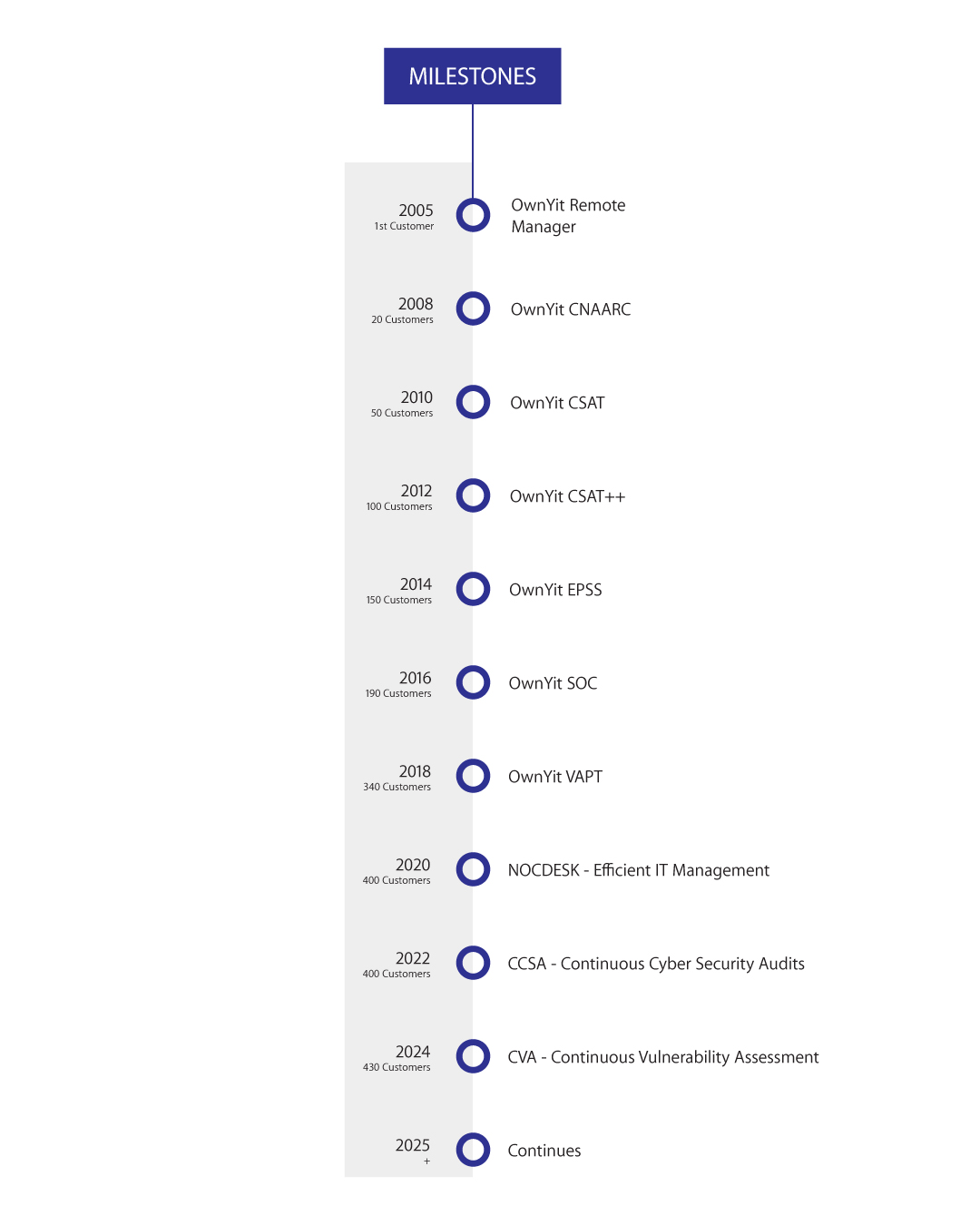
OwnYit has over 430 customers in 8 countries using our software to improve IT visibility, reduce IT operations costs, mitigate Cyber security risks, enable Cyber compliance, enhance DevOps collaboration and create new product and service offerings. With OwnYit our users break down traditional IT management paradigms and move from Micro-management of IT events to Root Cause Remediation.
IT Machine data is one of the most complex areas of big data. OwnYit CSAT turns IT Machine data into actionable inputs, no matter what business you're in. It's what we call Actionable Cyber Security.
ACS gives you a real-time visibility of what's happening across your IT systems and IT infrastructure and your users are doing that will immediately affect your IT systems. This allows you to make specific intelligent decisions that can immediately improve the Cyber Security of your organization.
Delivering continuous monitoring, automated assessments, and proactive management to strengthen IT security and optimize performance.




Our 430+ satisfied client
Continuous Cyber Security Audits
Continuous Vulnerability Assessment
Efficient IT Management
Collect, Connect, and Protect
Empowers decision-maker to analyze and monitor whether IT protocols and policies are being followed and take appropriate action when necessary.

Continuous Cyber Security Audits

Active Defence

Enhanced Security Posture

Compliance Assurance

Operational Efficiency

Risk Mitigation

Improved Security

Comprehensive Coverage
Explore how streamlined cyber security solutions can safeguard your business from evolving digital threats.
Learn how effective endpoint management can ensure your devices are secure and compliant in today's remote working world.
Understand the importance of cyber security audits and how to ensure your business stays compliant with evolving regulations.