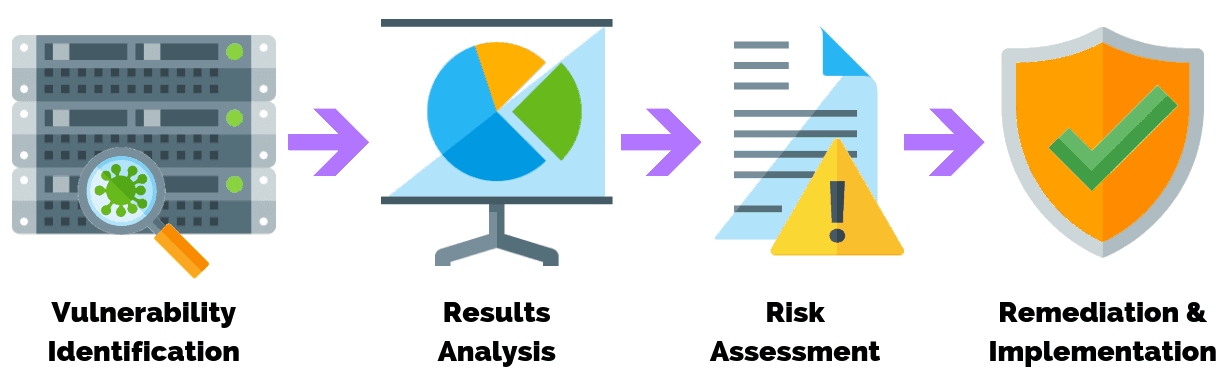
OwnYit VAPT is a tool which automates the process of identifying current vulnerabilities in an IT infrastructure while also helps in testing if any external vulnerabilities can penetrate the systems.
VAPT has its own process by which it scans systems and applications and understands potential weaknesses and threats that can be a major problem in an IT infrastructure.
This helps managers to be better equipped and take actionable steps in overcoming such problems in future.